In this article:
Introduction:
In a recent report commissioned by Tenable and conducted by Miercom, Tenable emerged as the top performer in various vulnerability management aspects. Among the most important things Tenable did well was provide the fastest and broadest coverage of CISA’s Known Exploited Vulnerabilities (KEV) catalog, which is an essential resource for determining which risk remediation tasks should be prioritized in light of the changing nature of cyber threats.
Tenable’s Superiority in CISA’s KEV Catalog
Tenable excels in vulnerability management, outperforming rivals in critical areas including quick and thorough coverage of the CISA’s list of known exploited vulnerabilities. These findings are the centerpiece of the “Vulnerability Management Competitive Assessment” report, an exclusive publication by Miercom at the behest of Tenable.
Prioritizing Risks with KEV Catalog
The KEV catalog is an invaluable resource for security teams, aiding them in the prioritization of risk remediation. With a slew of new Common Vulnerabilities and Exposures (CVEs) being disclosed in 2022, staying ahead of these threats is of paramount importance.
Tenable’s Unrivaled Performance
Tenable’s prowess doesn’t stop there; the report also underlines its dominance in other areas:
1️⃣ Broadest coverage of CVEs overall
2️⃣ Comprehensive coverage of CVEs for top 24 technology vendors
3️⃣ In-depth coverage of Center for Internet Security’s CIS Benchmarks configuration recommendations
Tenable’s consistency in delivering excellence in vulnerability management is unequivocal. As Miercom, a seasoned product testing firm with over three decades of experience, concludes, Tenable remains the unparalleled leader in this field.
Swift and Precise KEV Detection
Given the overwhelming risks present in organizational IT infrastructures, the ability to detect Known Exploited Vulnerabilities swiftly is paramount. Tenable not only offers the most comprehensive coverage of the KEV catalog but also updates its Vulnerability Management products, including Tenable Nessus, Tenable Security Center, and Tenable Vulnerability Management, faster than competitors. This ensures organizations can promptly respond to emerging threats.
Tenable’s Global Approach
At Tenable, our primary objective is to help customers pinpoint their cyber exposure gap with precision and expediency. To achieve this, our research teams span the globe, ensuring prompt and accurate coverage for emerging threats. Tenable diligently monitors and tracks updates to the CISA KEV catalog on a daily basis, prioritizing the development of new detections when necessary.
Efficient Scanning Process
In most cases, Tenable’s default scan policies automatically identify the majority of CISA KEVs, including newly added ones, without requiring any adjustments. However, a select few may necessitate minor modifications due to the nature and precision of detection.
Discovering CISA KEVs in Your Scan Results
Tenable offers multiple avenues for identifying CISA KEVs within your scan results, depending on your Tenable product:
1. For Tenable Nessus Essentials, Professional, or Expert customers, the CVE can be filtered in completed scan results, with reference information visible in the vulnerability detail view.
2. Tenable Security Center (version 5.20 and above) customers can employ “Cross References” filters to automatically search for plugins containing CVEs referenced in the KEV catalog.
Here’s how:
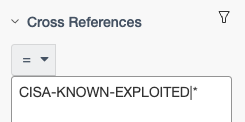
- Navigate to the “Analysis-Vulnerabilities” view and, if not already visible, add the “Cross References” filter.
- Enter the following:
CISA-KNOWN-EXPLOITED|*
(This command will display all plugins in your environment that are being tracked in the catalog.)
- Upon choosing the “Vulnerability Detail List” view, you’ll find the CISA reference along with the date displayed at the bottom right corner.

For more specific filtering, use examples like:
- CISA-KNOWN-EXPLOITED|2023/10/25
(KEV Findings due on October 25, 2023) - CISA-KNOWN-EXPLOITED|2023/*
(KEV Findings due in 2023) - CISA-KNOWN-EXPLOITED|2023/23/*
(KEV Findings due in October, 2023)
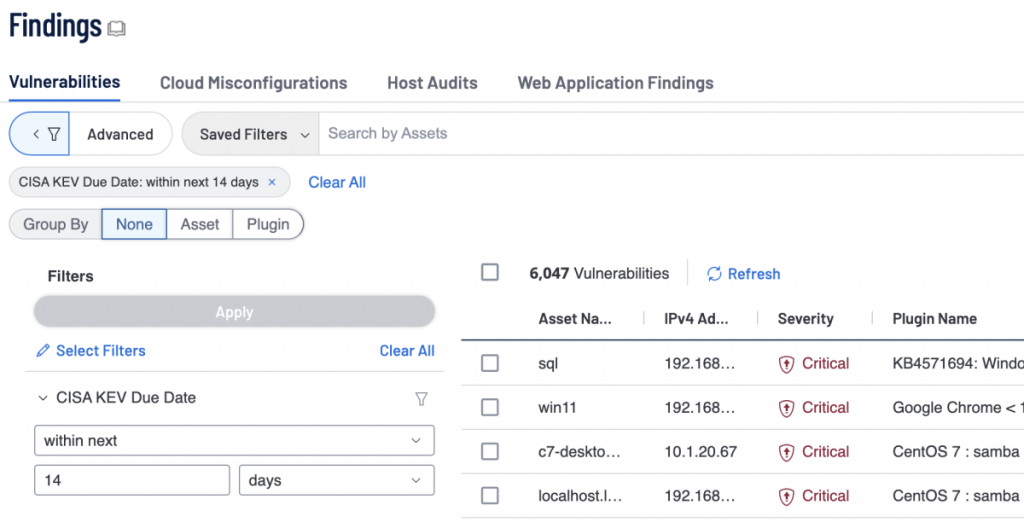
Tenable Vulnerability Management
Tenable Vulnerability Management customers may automatically search for results including CVEs listed in the KEV catalog by utilizing the “Due Date” filter in the “Explore – Findings” section. This filter may be included into dashboard or report widgets and supports relative date filters for both past and future due dates.
Conclusion
Tenable distinguishes itself from the competition by providing unmatched coverage and quick detection capabilities for vulnerabilities included in the CISA KEV Catalog. Clients gain from timely detections made possible by daily plugin upgrades. Users of Tenable Security Center and Tenable Vulnerability Management may now take use of extra capabilities that allow for thorough tracking and measurement of mitigation activities for KEV catalog vulnerabilities. Select Tenable for unrivaled cybersecurity solutions that are adjusted to counteract changing threats.
🔐 Secure your digital fortress with Tenable, the ultimate cybersecurity solution!
Act NOW and enjoy an incredible 30% OFF! Shield your business from threats TODAY.
Hurry, limited time offer! Protect what matters most! Don’t Miss Out!
FAQs
❓ What is a vulnerability management process?
A vulnerability management process refers to the continuous and systematic approach used to identify, assess, document, oversee, and resolve cybersecurity vulnerabilities within endpoints, workloads, and systems.
❓ What are the 4 stages of vulnerability management?
The vulnerability management process comprises four ongoing stages: identification, prioritization, remediation, and reporting. These stages are crucial for ensuring the effectiveness of the process. A vulnerability is a system flaw or weakness that, if exploited, could enable unauthorized access and potential attacks.
❓ What is risk remediation?
In Tenable’s context, risk remediation refers to the methodical handling of unanticipated project activities or circumstances that can possibly negatively impact remediation systems’ performance. The project team evaluates these risks unique to Tenable’s vulnerability management solutions inside the Tenable framework and creates strategic strategies to successfully mitigate these risks, guaranteeing optimal performance and security for enterprises utilizing Tenable products.
 iVoicesoft.com Software Review, Software Giveaway & Deals
iVoicesoft.com Software Review, Software Giveaway & Deals