Exposed management interfaces pose significant risks in the realm of cybersecurity, serving as potential entry points for malicious infiltration. In response to this threat, the Cybersecurity and Infrastructure Security Agency (CISA) issued Binding Operational Directive 23-02, directing U.S. federal agencies to remove such interfaces from the internet. This article investigates an innovative method for locating elusive devices with exposed management interfaces that makes use of the Service Location Protocol (SLP).

In this article:
Harnessing SLP to Uncover Vulnerable Management Interfaces
The Cybersecurity and Infrastructure Security Agency (CISA) recently unveiled the Binding Operational Directive (BOD) 23-02, directing U.S. federal agencies to disconnect management interfaces from the internet as a safeguard against potential risks. CISA defines a networked management interface as a dedicated device interface accessible via network protocols, exclusively designed for authorized users to perform administrative tasks on a device, a group of devices, or the entire network.
- Proprietary Nature: Networked management interfaces often vary by vendor and can easily blend in with the myriad of legitimate services offered by an organization.
- Lack of Public Vulnerabilities: Some networked management interfaces may not have associated public vulnerabilities, making them invisible to standard vulnerability management programs.
While there are a number of ways to find internet-exposed networked management interfaces, this article offers a unique strategy that works especially well for finding devices that are difficult to find.
Utilizing Service Location Protocol (SLP)
SLP (Service Location Protocol) is used to discover network service information. It involves two types of agents: service agents (SA) for single-host services and directory agents (DA) for multi-host services. SLP covers a range of services. Tenable Vulnerability Management plugins, previously Tenable[dot]io, Tenable Security Center, and Tenable Nessus, are used to send SLP requests and analyze results. These plugins include:
- Plugin ID 23778: SLP Server Detection (UDP)
- Plugin ID 23777: SLP Server Detection (TCP)
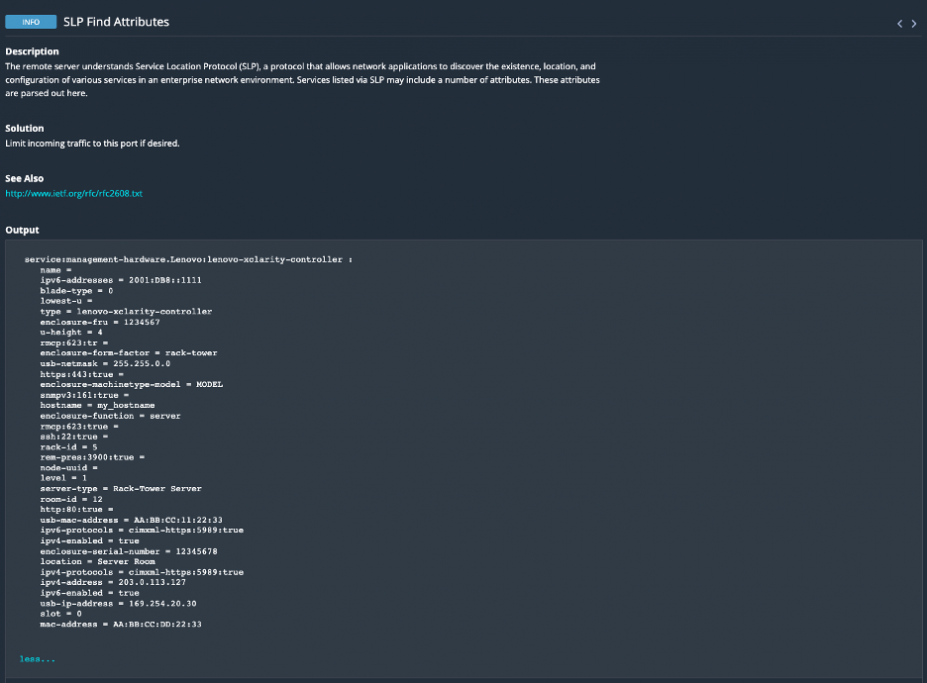
- Plugin ID 175142: SLP Find Attributes
The first two plugins reveal if the remote host runs SLP, its role as a directory or service agent, and the services it offers. The third plugin requests attributes for each service discovered, potentially providing valuable information. Analysis may be needed for service-specific or ad-hoc attributes. This scanning process can uncover hosts inadvertently leaking information.
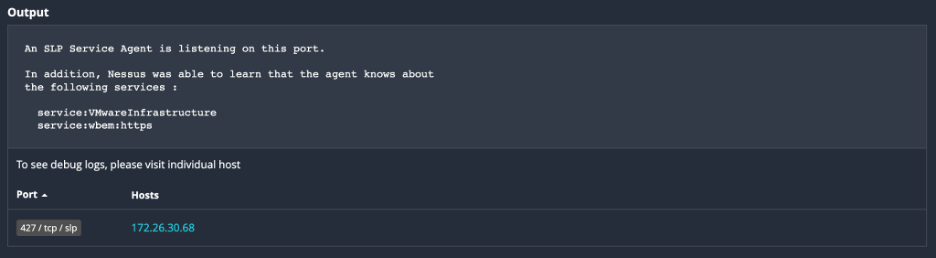
An example of Plugin 23778 demonstrating the presence of SLP services.
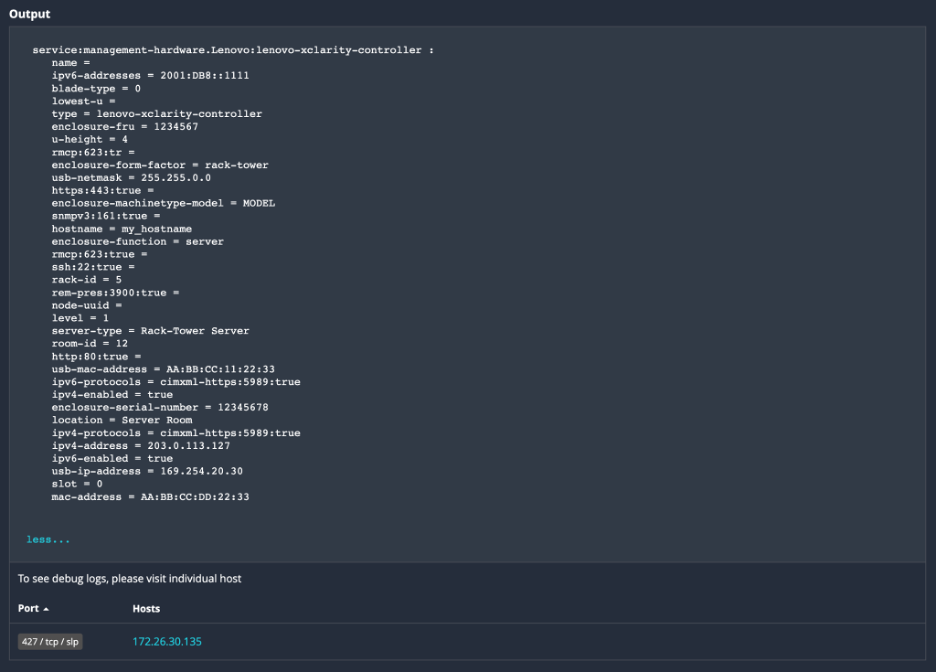
An example of Plugin 175142 revealing attributes associated with SLP services.
Identifying Management Interfaces
Out-of-band server management interfaces, such as integrated management module (IMM), integrated lights-out (iLo) and integrated Dell remote access controller (iDRAC), can be observed by SLP. It can also identify management interfaces for storage devices, printers and more. The following list of SLP services may include attribute information relating to networked management interfaces:
SLP Service Name – Associated Exposure
- service:VMwareInfrastructure – VMWare ESX & ESXi
- service:cmm.smci – Supermicro Update Manager (SUM)
- service:api:https – Dell and HPE storage
- service:lenovo-smm – Lenovo System Management Module
- service:management-hardware.Lenovo:lenovo-xclarity-controller – Lenovo xclarity Controller
- service:x-mgmt.avago:lsa – Intel/Avago RAID Management
- service:raid.001378:http – Storage devices (QSAN, etc)
- service:printer – Printers
- service:management-hardware.IBM:integrated-management-module2 – IBM Management Module
While more services are worth exploring, these are among the most prevalent ones.
After a quick internet scan targeting services like “management-hardware” or “management-software,” a number of active hosts were discovered. The observed SLP service names and their respective occurrences are as follows:
- 10,611 occurrences of “service:VMwareInfrastructure”
- 61 occurrences of “service:management-hardware.IBM:integrated-management-module2”
- 58 occurrences of “service:management-hardware.Lenovo:lenovo-xclarity-controller”
- 3 occurrences of “service:management-software.IBM:platform-agent”
- 3 occurrences of “service:management-hardware.IBM:integrated-management-module”
- 1 occurrence of “service:management-software.IBM:hardware-management-console”
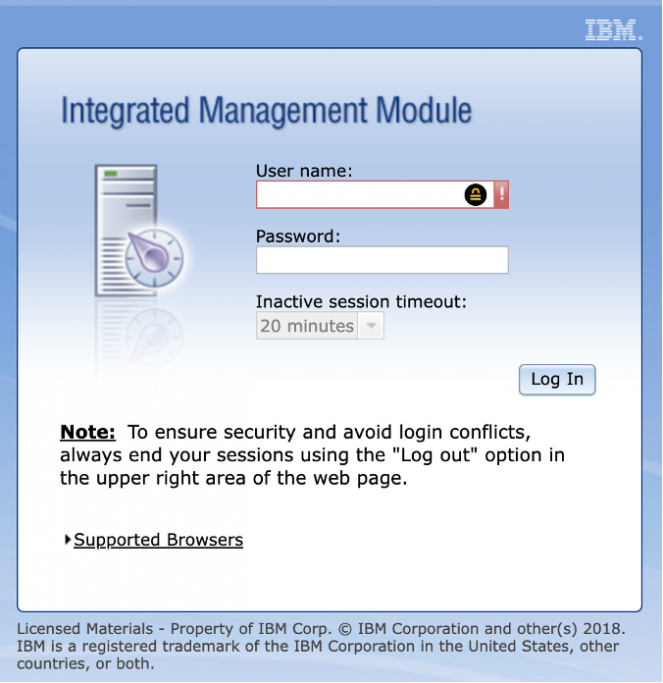
For instance, a device uncovered by this scan is displayed in the screenshot below, showcasing its web interface.
Furthermore, some of these exposed services may also disclose both internal and external IP addresses, providing additional insights into their network configuration.
service:raid.001378:http
(vendor=Qsan Technology),(model=PerseusAPL),(product=XN3004T),(type=UNIFIED),(hostname=XXXXXX),(version=3.4.2),(builddate=202211290200),(dev=LAN1),(link=Up),(ip=192.168.X.X),(remoteip=XXX.XXX.XXX),(mac=00:13:78:XX:XX:XX),(serial=XXXXXXXXXX),(httpPort=13080),(httpsPort=13443),(webReady=Yes),(flags=0x3),(bpl=XXXX),(qlinkHost=),(qlinkPort=)
A QSAN NAS device is detected hosting a management interface accessible both internally and over the internet through ports 13080 and 13443, aligning with the documented management interfaces associated with these devices.
In Nessus scans, the results will be displayed as shown below:
Conclusion
Because attackers value these entry points, it is critical for security to identify exposed management interfaces. It is highly recommended to use SLP Nessus plugins during external scans, even with this task’s complexity. Companies need to carefully review plugin outputs, making sure that the IPs and ports are correct to make sure there is no exposure to the internet. It’s also critical to evaluate whether the disclosed information complies with organizational standards. CISA intends to search U.S. federal agencies for these kinds of exposures, and using a variety of identification techniques helps all organizations comprehend and reduce risks. Comprehensive security efforts benefit from the use of vulnerability management tools such as Tenable Attack Surface Management and Nessus perimeter scans.
🔥 Don’t miss out on unbeatable security with Tenable!
Safeguard your digital world NOW and enjoy a jaw-dropping 25% OFF!
Limited time offer! Hurry, protect your assets TODAY!
FAQs
❓ What is the service location protocol SLP RFC 2608?
The Service Location Protocol (SLP, defined in RFC 2608) enables an unauthenticated remote attacker to register arbitrary services. This vulnerability could potentially enable the use of spoofed UDP traffic for launching a denial-of-service (DoS) attack, significantly amplifying its impact.
❓ What is attack surface monitoring?
Attack surface monitoring is a security tactic that entails the continuous detection and observation of possible attack points as interpreted by possible threat actors.
❓ What is the management interface?
A management interface, is a means for network operators to oversee and administer the devices within their networks. It grants access to control, configuration, and status information for each device, facilitating effective network management.
 iVoicesoft.com Media Software Review
iVoicesoft.com Media Software Review



